CỘNG ĐỒNG AN NINH MẠNG VIỆT NAM
@ 2009 - 2021 Bkav Corporation
Install the app
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Tổng hợp Write-up cuộc thi WhiteHat Summer Contest 2017
- Bắt đầu sunny
- Ngày bắt đầu
Writeup Cat Ba island | Lĩnh vực: Cryptography | Số đội giải được 23 | Số điểm 200
--hackmymoney--
How well can you cheat? Want to kayak in Cat Ba island?
Netcat: nc hackmymoney.wargame.whitehat.vn 1337
http://material.wargame.whitehat.vn/contests/13/hackmymoney.zip
<md5:3b611cd82cf9d7e63a61f4fad317b216>
Backup:
nc backup.wargame.whitehat.vn 31001
http://bak.material.wargame.whitehat.vn/contests/13/hackmymoney.zip
<md5:3b611cd82cf9d7e63a61f4fad317b216>
--hackmymoney--
How well can you cheat? Want to kayak in Cat Ba island?
Netcat: nc hackmymoney.wargame.whitehat.vn 1337
http://material.wargame.whitehat.vn/contests/13/hackmymoney.zip
<md5:3b611cd82cf9d7e63a61f4fad317b216>
Backup:
nc backup.wargame.whitehat.vn 31001
http://bak.material.wargame.whitehat.vn/contests/13/hackmymoney.zip
<md5:3b611cd82cf9d7e63a61f4fad317b216>
Mã:
#!/usr/bin/env python2
from pwn import * # https://pypi.python.org/pypi/pwntools
import argparse
parser = argparse.ArgumentParser()
parser.add_argument('host', nargs='?', default='hackmymoney.wargame.whitehat.vn')
parser.add_argument('port', nargs='?', default=1337, type=int)
parser.add_argument('--log-level', default='debug')
args = parser.parse_args()
context.log_level = args.log_level
p = remote(args.host, args.port)
def get_secret_code():
p.recvuntil('Choose:\n')
p.sendline('1')
p.recvuntil('Your secret code: ')
code = p.recvline().rstrip()
log.info('Your secret code: %s', (code))
return code
def get_money(secret_code):
p.recvuntil('Choose:\n')
p.sendline('2')
p.recvuntil('Give me your secret code: \n')
p.sendline(secret_code)
result = p.recvuntil(' ').strip()
if result == 'Can':
log.info('Can not get money')
return None
else:
assert result == 'You'
p.recvuntil('got:')
got = p.recvline().strip()
log.info('You got: %s', repr(got))
p.recvuntil('You have: ')
have = int(p.recvline().rstrip())
log.info('You have: %d', have)
return got
code = get_secret_code()
iv = bytearray(code.decode('hex'))
log.info('iv: %s', repr(iv))
got = get_money(bytes(iv).encode('hex'))
assert got == '1'
iv[4] ^= 88
iv[5] ^= 8
iv[6] ^= 88
iv[7] ^= 88
iv[8] ^= 75
iv[9] ^= 64
iv[10] ^= 80
iv[11] ^= 88
iv[12] ^= 64
iv[13] ^= 64
iv[14] ^= 24
got = get_money(bytes(iv).encode('hex'))
while True:
n = random.randint(0, 255)
log.info('xor: %d', n)
modified_iv = bytearray(iv)
modified_iv[3] ^= n
modified_got = get_money(bytes(modified_iv).encode('hex'))
if modified_got is not None and int(modified_got) > int(got):
breakNguồn Kimiyuki Blog
Chỉnh sửa lần cuối:
Comment
Writeup Da Nang | Lĩnh vực: Cryptography | Số đội giải được 19 | Số điểm 200
Please help me to find the flag??????
Downloadfile:
http://material.wargame.whitehat.vn/contests/13/DaNang.zip
Backup:
http://bak.material.wargame.whitehat.vn/contests/13/DaNang.zip
Dùng công cụ Python Undecompyle 6 để khôi phục source code
Decrypt
Please help me to find the flag??????
Downloadfile:
http://material.wargame.whitehat.vn/contests/13/DaNang.zip
Backup:
http://bak.material.wargame.whitehat.vn/contests/13/DaNang.zip
Dùng công cụ Python Undecompyle 6 để khôi phục source code
Mã:
$ uncompyle6 makefile.pyc
# uncompyle6 version 2.9.11
# Python bytecode 2.7 (62211)
# Decompiled from: Python 3.5.2 (default, Nov 17 2016, 17:05:23)
# [GCC 5.4.0 20160609]
# Embedded file name: /root/Desktop/ctf-2017/rade/makefile.py
# Compiled at: 2017-04-21 20:42:38
from FLAG import *
from Crypto.Util.number import *
p = getPrime(1024)
q = getPrime(1024)
n = p * q
e1 = 17
e2 = 23
m1 = pow(flag, e1, n)
m2 = pow(flag, e2, n)
c1 = pow(m1 + 12345, e1, n)
c2 = pow(m1 + 56789, e1, n)
c3 = pow(m2 + 12345, e2, n)
c4 = pow(m2 + 56789, e2, n)
# okay decompiling makefile.pyc
Mã:
#!/usr/bin/env python2
import scryptos
import gmpy2
import Crypto.Util.number
n = 23992456508721632904544057999056395984840598682551527471151904763246778638836805311058576074076544471814362118450963752614808101805018226501728749753154687251596663180454809994272928278066817153483685668132338944992849111855590973474678454159123639456555256485147196164078477717189520027988101925788303558976065942012105491523422884349644306896086216721825961334666043695121350988761613913914655313225263251356627080558127266206207253980892813908459449433940028268804981985006285644508736389967109173883994849116220035021283230523958640143355551140077459561176550844398278642511471910168765368624465988996082307992457
c1 = 20373828497176435167633953604896280749084861536083536617122139289929021045377176745113967394233342868062933415554192920963948057887324013008257380015103546511196207444982065505097904316167335975881412955740451727799394577357107415462104942067847048630173382510001061068806873459709567970640047451719077689284250663779574472232440594570502056709748603086893912068708152949459839465110567129133452824619222918019880393381073202052633467737917229789195417254877277542398992729106705037414050409175283815504552780234997208287185820010853470529752628470226853313501197054312938111140137899570545855875031148908922559079288
c2 = 4360293477491071631082413589399984151934700148049881396354060511784164719699104502640364063839372357371432182276578283932647249629707984639755245731994004982047010862474568253438883825981211552726455647610616600152683140602219777227764342827766552684058977170125324805316413550680703753463380261978903747369677517090549750490497714726106808405188795507741435252228742048791254891796083781713724953974101730953449734214103419451007355326070889428042830527374106171411884042865409718813225704924308910578917985370161732700040769553579304781551439507813917217693054553136139858632877393572913681604198562756394542739717
c3 = 4345261358659519189634881349240932351623603440440060460588285817392306152201826610576491755629698765088135761317793967803519010356869269204503397215039512744495117601932620637450095192646479479541571697381615227131485964855439316795397514445542660502760126364064850197352955455820341422106740318181122113707487426652989875585231637716536188004952356846847687782788196021954904944243050038759261831381697585862182084930662578928342538660648403902072793943235882313263403348511364765676275877687747514403142706712995406077875195587485333137738286810493929324782535392363155178660765334428891921464976278013274433592459
c4 = 11163192691864487842504791707572292045010440994593022973064948393324184598662086767886111478358067883324039072186651857397731078118781186686459647088206129240315423019956385054334592265029781917246602461962626683725203283354094411740566113019140776580459728655850754495232498348144806199874330892136766891492831287879346899778473534258469040357585649045269842028785546606058644151580331160754603828262995696611984149905299109630697269974668616156412842759609194334129212734919638779629261074770920807952993453659743525451175541328430753432209789806184520128139906770561431423993324872179142853918272022140840732281811
e1 = 17
e2 = 23
a = 1
b1 = 12345
b2 = 56789
rsa1 = scryptos.crypto.RSA(e1, n)
rsa2 = scryptos.crypto.RSA(e2, n)
m1 = scryptos.crypto.attack.rsautil.franklin_reiter(rsa1, a, b2 - b1, c1, c2) - b1
m2 = scryptos.crypto.attack.rsautil.franklin_reiter(rsa2, a, b2 - b1, c3, c4) - b1
assert pow(m1 + 12345, e1, n) == c1
assert pow(m1 + 56789, e1, n) == c2
assert pow(m2 + 12345, e2, n) == c3
assert pow(m2 + 56789, e2, n) == c4
assert -4 * e1 + 3 * e2 == 1
flag = pow(gmpy2.invert(m1, n), 4, n) * pow(m2, 3, n) % n
assert pow(flag, e1, n) == m1
assert pow(flag, e2, n) == m2
print(Crypto.Util.number.long_to_bytes(flag))Nguồn Kimiyuki Blog
Chỉnh sửa lần cuối:
Comment
Quang Ngai | Lĩnh vực: Forensics | Số đội giải được 21 | Số điểm 100
What’s the collection hiding?
Download file:
http://material.wargame.whitehat.vn/contests/13/QuangNgai.zip
<md5:bf70a33a42b87edd532a274992bd7a08>
Backup:
http://bak.material.wargame.whitehat.vn/contests/13/QuangNgai.zip
<md5:bf70a33a42b87edd532a274992bd7a08>
Tải về giải nén, mở bằng hex xem header file
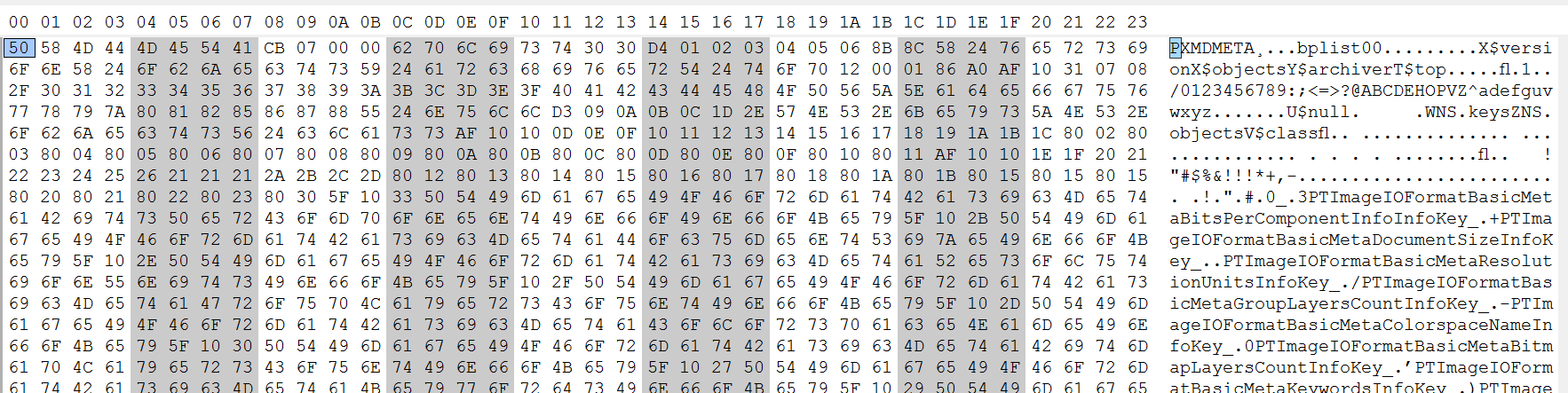 Search google .PXM và nhận được kết quả
Search google .PXM và nhận được kết quả
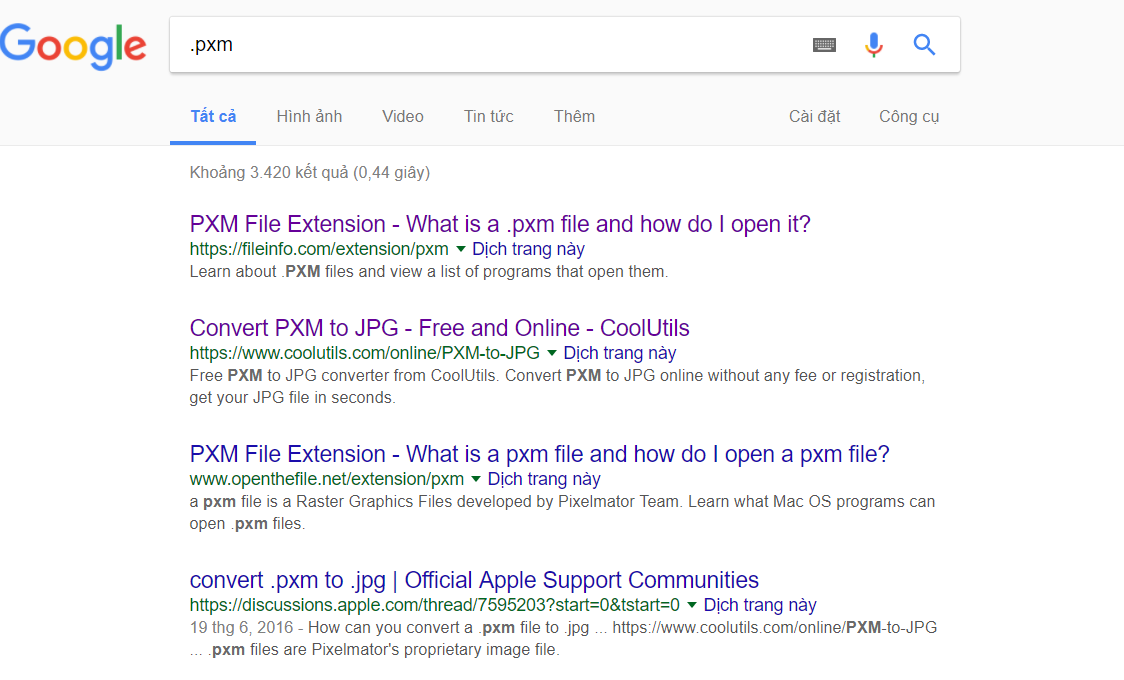
Tiếp tục search với tên của nhà phát triển
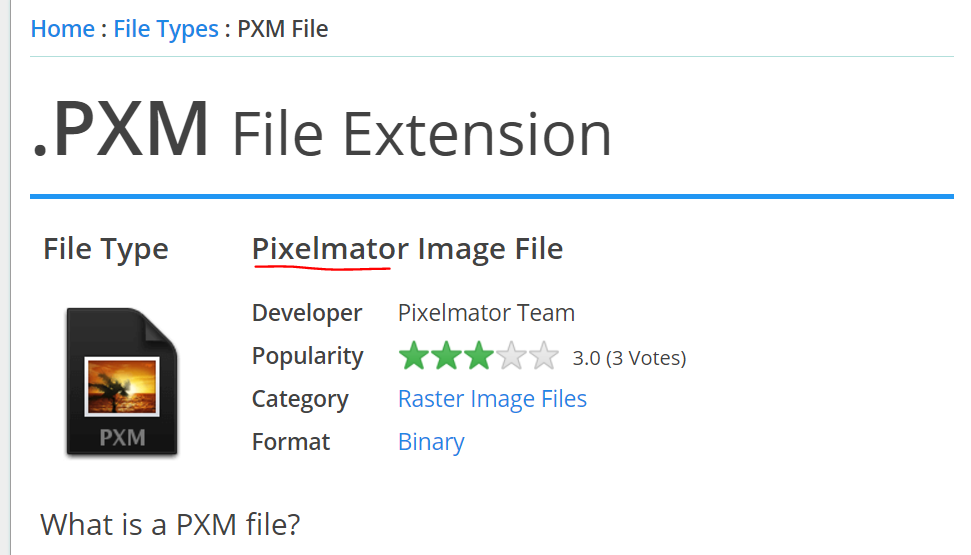 Tìm được trang chủ của ứng dụng này,
Tìm được trang chủ của ứng dụng này,
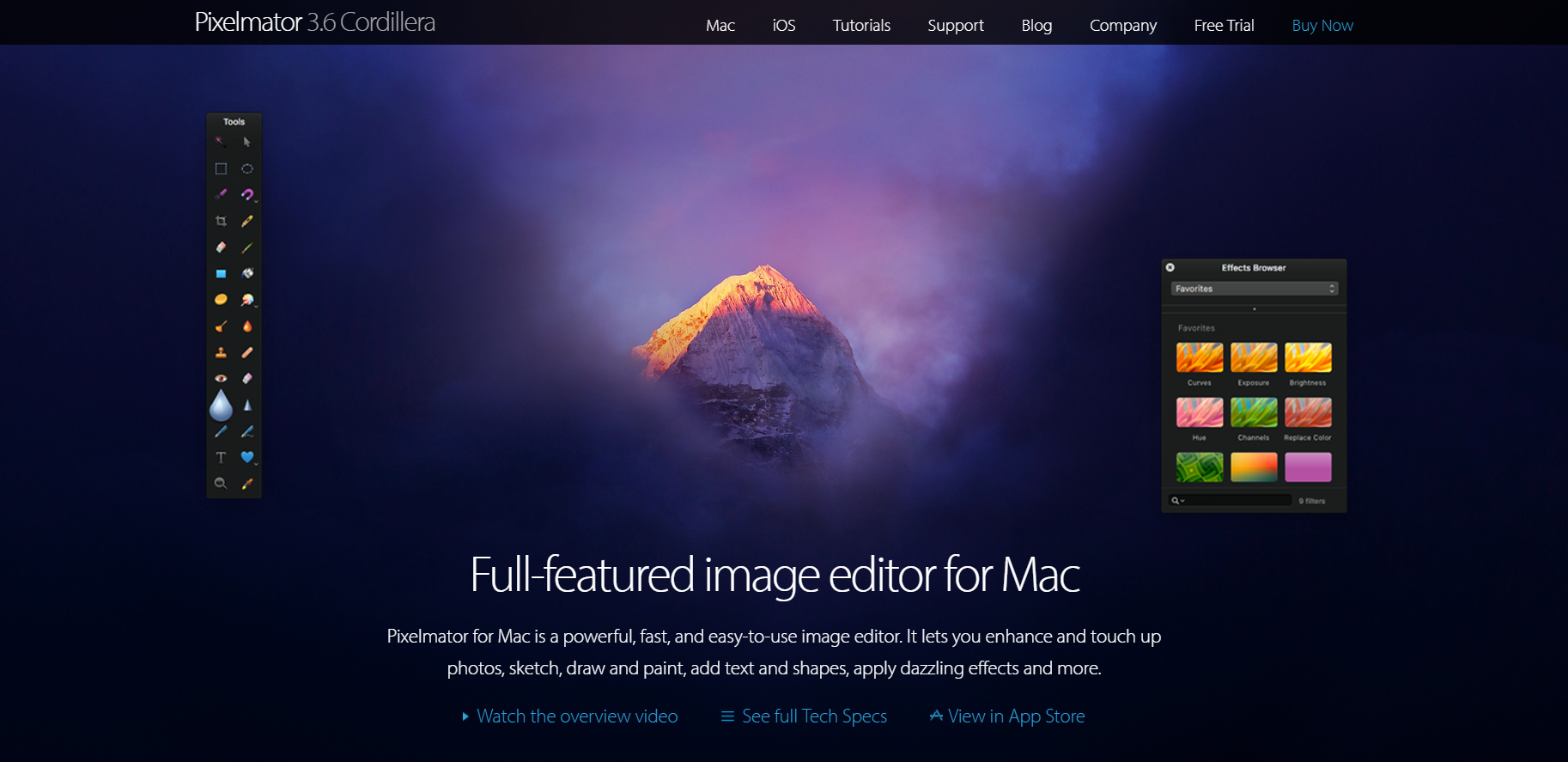 Tải về cài đặt, đổi tên file ban đầu thành data.pxm
Tải về cài đặt, đổi tên file ban đầu thành data.pxm

What’s the collection hiding?
Download file:
http://material.wargame.whitehat.vn/contests/13/QuangNgai.zip
<md5:bf70a33a42b87edd532a274992bd7a08>
Backup:
http://bak.material.wargame.whitehat.vn/contests/13/QuangNgai.zip
<md5:bf70a33a42b87edd532a274992bd7a08>
Tải về giải nén, mở bằng hex xem header file
Tiếp tục search với tên của nhà phát triển

Chỉnh sửa lần cuối:
Comment
Writeup Ha Long bay - Cryptography - 250 điểm
Description:
Tải file về và giải nén file RSA.zip ta có 2 file data.txt và encrypt.py.
File encrypt.py
Ta thấy đây là đoạn mã python dùng để mã hóa flag bằng key RSA tự sinh. Flag có độ dài nhỏ hơn 18 byte và được chia thành 3 phần gắn vào 1 xâu cố định, giữa 2 phần có nối bằng một byte ngẫu nhiên, từ đó ta có 3 xâu và mã hóa bằng khóa RSA để được 3 đoạn mã. Thông tin khóa công khai có trong file data.txt:
Để ý khóa RSA dùng số mũ công khai e = 3 . Ta có thể dùng các tấn công hệ mã RSA với số mũ nhỏ để giải bài này.
Cụ thể ta dùng Coppersmith's Short Pad để lấy hiệu các phần flag sau đó dùng Franklin-Reiter Related Message để tìm giá tri flag. Chi tiết các bạn có thể xem ở tài liệu Twenty Years of Attacks on the RSA Cryptosystem của Dan Boneh (phần 4.3 và 4.4).
Code: solve.sage
Description:
Mã:
Decrypt the following code before enjoying your summer days at one of the most beautiful bays in the world - Ha Long bay.
Download file here:
http://material.wargame.whitehat.vn/contests/13/RSA.zip
<md5:c6658022c6d9761ffa636fc6872ee85b>
Backup:
http://bak.material.wargame.whitehat.vn/contests/13/RSA.zip
<md5:c6658022c6d9761ffa636fc6872ee85b>Tải file về và giải nén file RSA.zip ta có 2 file data.txt và encrypt.py.
File encrypt.py
from Crypto.Util import number
from secret import M, flag
p = number.getPrime(512)
q = number.getPrime(512)
n = p * q
e = 3
assert (len(flag) < 18),"Fail!"
fsplit = len(flag)/3
m1 = M + chr(number.getRandomRange(32, 128)) + flag[:fsplit]
m2 = M + chr(number.getRandomRange(32, 128)) + flag[fsplit:2*fsplit]
m3 = M + chr(number.getRandomRange(32, 128)) + flag[2*fsplit:]
m1 = int(m1.encode('hex'),16)
m2 = int(m2.encode('hex'),16)
m3 = int(m3.encode('hex'),16)
C1 = pow(m1, e, n)
C2 = pow(m2, e, n)
C3 = pow(m3, e, n)
from secret import M, flag
p = number.getPrime(512)
q = number.getPrime(512)
n = p * q
e = 3
assert (len(flag) < 18),"Fail!"
fsplit = len(flag)/3
m1 = M + chr(number.getRandomRange(32, 128)) + flag[:fsplit]
m2 = M + chr(number.getRandomRange(32, 128)) + flag[fsplit:2*fsplit]
m3 = M + chr(number.getRandomRange(32, 128)) + flag[2*fsplit:]
m1 = int(m1.encode('hex'),16)
m2 = int(m2.encode('hex'),16)
m3 = int(m3.encode('hex'),16)
C1 = pow(m1, e, n)
C2 = pow(m2, e, n)
C3 = pow(m3, e, n)
Ta thấy đây là đoạn mã python dùng để mã hóa flag bằng key RSA tự sinh. Flag có độ dài nhỏ hơn 18 byte và được chia thành 3 phần gắn vào 1 xâu cố định, giữa 2 phần có nối bằng một byte ngẫu nhiên, từ đó ta có 3 xâu và mã hóa bằng khóa RSA để được 3 đoạn mã. Thông tin khóa công khai có trong file data.txt:
n = 103812409689464886276475047044770609297885893720146571798654593885477457188425375786047017735691464865799751262776976174291152757506033948402223696021505470811665108707476725788296289255777914656800454451779117367605227364391483323666809650532860469176398816220707851639905500304208833022438234033264200398959
e = 3
C1 = 9317106922634505445328279149755295612464875825943780841886193649700131610057100771444165757592479299555845021862440454968502065319770337331674061960123779876709748994547507057835826773522733671492329400557540100987018908395372213360970889608191940631081957498661950679566048064234326337242245437800870328713
C2 = 9314352234311777268152500810432217195086739647228997430466360767070638972017377674642639833356580951663634114522574738957708645348438979256455824440476178459296267056062724307782801856615506577790281367843133061096735566462588088807072141910079117362448136849082448630141871675817981866725491776400151339928
C3 = 102298788718908831383454512674839558060033746080468660252243145800572734468521296602058538109452538907204027081338987796558296639830757629468491322438048912956916198524821066676689795698612028521062296901313097979278633376983280108123961097977187251599033620058543603046291262367128490175209233898073639549204
e = 3
C1 = 9317106922634505445328279149755295612464875825943780841886193649700131610057100771444165757592479299555845021862440454968502065319770337331674061960123779876709748994547507057835826773522733671492329400557540100987018908395372213360970889608191940631081957498661950679566048064234326337242245437800870328713
C2 = 9314352234311777268152500810432217195086739647228997430466360767070638972017377674642639833356580951663634114522574738957708645348438979256455824440476178459296267056062724307782801856615506577790281367843133061096735566462588088807072141910079117362448136849082448630141871675817981866725491776400151339928
C3 = 102298788718908831383454512674839558060033746080468660252243145800572734468521296602058538109452538907204027081338987796558296639830757629468491322438048912956916198524821066676689795698612028521062296901313097979278633376983280108123961097977187251599033620058543603046291262367128490175209233898073639549204
Để ý khóa RSA dùng số mũ công khai e = 3 . Ta có thể dùng các tấn công hệ mã RSA với số mũ nhỏ để giải bài này.
Cụ thể ta dùng Coppersmith's Short Pad để lấy hiệu các phần flag sau đó dùng Franklin-Reiter Related Message để tìm giá tri flag. Chi tiết các bạn có thể xem ở tài liệu Twenty Years of Attacks on the RSA Cryptosystem của Dan Boneh (phần 4.3 và 4.4).
Code: solve.sage
Mã:
# source code http://inaz2.hatenablog.com/entry/2016/01/20/022936
def short_pad_attack(c1, c2, e, n):
PRxy.<x,y> = PolynomialRing(Zmod(n))
PRx.<xn> = PolynomialRing(Zmod(n))
PRZZ.<xz,yz> = PolynomialRing(Zmod(n))
g1 = x^e - c1
g2 = (x+y)^e - c2
q1 = g1.change_ring(PRZZ)
q2 = g2.change_ring(PRZZ)
h = q2.resultant(q1)
h = h.univariate_polynomial()
h = h.change_ring(PRx).subs(y=xn)
h = h.monic()
kbits = n.nbits()//(2*e*e)
diff = h.small_roots(X=2^kbits, beta=0.5)[0] # find root < 2^kbits with factor >= n^0.5
return diff
def related_message_attack(c1, c2, diff, e, n):
PRx.<x> = PolynomialRing(Zmod(n))
g1 = x^e - c1
g2 = (x+diff)^e - c2
def gcd(g1, g2):
while g2:
g1, g2 = g2, g1 % g2
return g1.monic()
return -gcd(g1, g2)[0]
if __name__ == '__main__':
n = 103812409689464886276475047044770609297885893720146571798654593885477457188425375786047017735691464865799751262776976174291152757506033948402223696021505470811665108707476725788296289255777914656800454451779117367605227364391483323666809650532860469176398816220707851639905500304208833022438234033264200398959
e = 3
C1 = 9317106922634505445328279149755295612464875825943780841886193649700131610057100771444165757592479299555845021862440454968502065319770337331674061960123779876709748994547507057835826773522733671492329400557540100987018908395372213360970889608191940631081957498661950679566048064234326337242245437800870328713
C2 = 9314352234311777268152500810432217195086739647228997430466360767070638972017377674642639833356580951663634114522574738957708645348438979256455824440476178459296267056062724307782801856615506577790281367843133061096735566462588088807072141910079117362448136849082448630141871675817981866725491776400151339928
C3 = 102298788718908831383454512674839558060033746080468660252243145800572734468521296602058538109452538907204027081338987796558296639830757629468491322438048912956916198524821066676689795698612028521062296901313097979278633376983280108123961097977187251599033620058543603046291262367128490175209233898073639549204
nbits = n.nbits()
kbits = nbits//(2*e*e)
print "padding lenght %d bytes " % (kbits/8)
print "upper %d bits (of %d bits) is same" % (nbits-kbits, nbits)
diff = short_pad_attack(C1, C2, e, n)
print "difference of two messages C1 and C2 is %d" % diff
m = related_message_attack(C1, C2, diff, e, n)
M1 = hex(int(m))[2:-1].decode('hex')
M2 = hex(int(m+diff))[2:-1].decode('hex')
print "Message of C1 is ", M1
print "Message of C2 is ", M2
diff = short_pad_attack(C1, C3, e, n)
print "difference of two messages C1 and C3 is ", diff
M3 = hex(int(m+diff))[2:-1].decode('hex')
print "Message of C3 is ", M3
print "Flag: ", M1[-5:] + M2[-5:] +M3[-5:]
Chỉnh sửa lần cuối:
Comment
Bài Con Dao islands, đầu tiên bạn phải tìm password cho file zip trong file Password.txt. Nếu bạn muốn một gợi ý thì mình đưa từ khóa "Brainfuck+". Còn chưa rõ thì bạn có thể xem ở đây.
Comment
Bài Con Dao islands, đầu tiên bạn phải tìm password cho file zip trong file Password.txt. Nếu bạn muốn một gợi ý thì mình đưa từ khóa "Brainfuck+". Còn chưa rõ thì bạn có thể xem ở đây.
Bài Con Dao islands, đầu tiên bạn phải tìm password cho file zip trong file Password.txt. Nếu bạn muốn một gợi ý thì mình đưa từ khóa "Brainfuck+". Còn chưa rõ thì bạn có thể xem ở đây.
Cảm ơn bạn nhiều,
Comment
Cho em hỏi là bài crypto Da Nang 200 điểm cách decrypt là như thế nào vậy ạ. Em đọc write-up phía trên không có hiểu gì cả.
Comment
Có lẽ bạn nên học về mã hóa RSA. Mình thì không chuyên về Crypto nhưng mình thấy có thông tin này hữu ích này.Cho em hỏi là bài crypto Da Nang 200 điểm cách decrypt là như thế nào vậy ạ. Em đọc write-up phía trên không có hiểu gì cả.
https://en.wikipedia.org/wiki/Coppersmith's_attack#Franklin-Reiter_related-message_attack
Comment
